This module introduces the fundamental concepts of network security, emphasizing the critical importance of protecting modern network infrastructures. Students will explore the current threat landscape, understand various attack vectors, and learn about comprehensive security measures across different network topologies including Campus Area Networks (CANs), SOHO, WAN, Data Centers, and Cloud environments.
📋 Overview
🔑 Key Terms
Attack Vector
A path by which a threat actor can gain access to a server, host, or network. Can originate from inside or outside the corporate network.
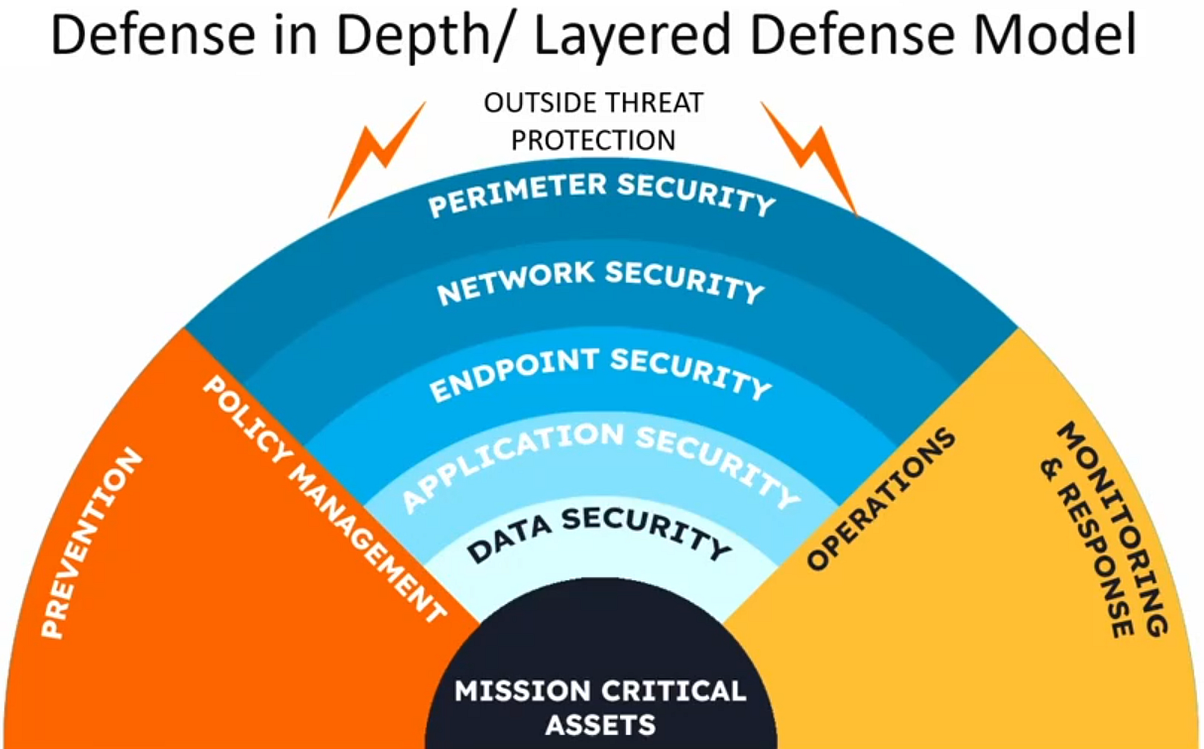
Defense-in-Depth
A security strategy that uses multiple layers of defense to protect network resources from various threats.
Data Loss Prevention (DLP)
Controls that combine strategic, operational, and tactical measures to prevent unauthorized data exfiltration.
Campus Area Network (CAN)
Interconnected LANs within a limited geographic area, typically within a single organization's premises.
BYOD
Bring Your Own Device - trend where employees use personal devices to access enterprise information and applications.
Mobile Device Management (MDM)
Features that secure, monitor, and manage mobile devices including corporate-owned and employee-owned devices.
Current State of Affairs
Networks Under Attack
Networks are routinely under attack, with organizations facing constant threats that can disrupt business operations, cause data loss, and compromise information integrity. Network security breaches can result in:
- Lost revenue for corporations
- Theft of intellectual property
- Legal action and lawsuits
- Threats to public safety
- Brand damage and loss of reputation
Internal vs External Threats
Internal threats can cause greater damage than external threats because internal users have direct access to building infrastructure and may possess knowledge of corporate networks and confidential data.
Common Data Loss Vectors
| Vector | Description |
|---|---|
| Email/Social Networking | Most common vector including instant messaging and social media sites |
| Unencrypted Devices | Stolen corporate laptops containing unencrypted confidential data |
| Cloud Storage | Compromised cloud access due to weak security settings |
| Removable Media | Unauthorized data transfer to USB drives or lost storage devices |
| Hard Copy | Improperly disposed confidential documents |
| Improper Access Control | Stolen or weak passwords providing easy access to corporate data |
Network Topology Overview
Campus Area Networks (CANs)
Interconnected LANs within limited geographic areas using defense-in-depth approach with multiple security layers:
- VPN for data confidentiality and integrity
- ASA Firewall for stateful packet filtering
- IPS for continuous traffic monitoring
- Secured Layer 2/3 switches with ACLs
- AAA servers for authentication
- ESA/WSA for email and web security
Small Office/Home Office (SOHO)
Protected using consumer-grade routers with basic security features:
- Integrated firewall features
- Secure wireless connections with WPA2
- Port security on access switches
- Antivirus and antimalware on hosts
Wide Area Networks (WANs)
Span wide geographical areas requiring secure transport over public networks:
- ASA devices for stateful firewall protection
- Secure VPN tunnels between sites
- Hardened ISRs at branch locations
- Always-on VPN connections
🏢 Data Center Networks
Off-site facilities storing sensitive data with comprehensive physical security:
- Outside perimeter: security officers, fences, surveillance
- Inside perimeter: motion detectors, security traps
- Biometric access controls
- High-speed Cisco Nexus switches
☁️ Cloud Networks
Virtualized environments extending organizational capabilities:
- Server virtualization with VMs
- Cisco Secure Data Center solution
- Secure segmentation and threat defense
- Protection against hyperjacking and antivirus storms
BYOD and Borderless Networks
Supporting mobile device access with MDM features:
- Data encryption enforcement
- PIN enforcement
- Remote data wipe capabilities
- Jailbreak/root detection
Case Study: Enterprise Network Security Implementation
Multi-Site Corporate Network
A multinational corporation implements comprehensive network security across their infrastructure including main campus, branch offices, data centers, and remote workers. The implementation includes ASA firewalls at each site, site-to-site VPN tunnels, centralized AAA authentication, and MDM for BYOD devices.
This case demonstrates the practical application of defense-in-depth principles across various network topologies, showing how different security technologies work together to provide comprehensive protection.
Common Pitfalls & Misconceptions
Relying on Perimeter Security Only
Many organizations focus solely on perimeter defenses, ignoring internal threats and the need for defense-in-depth strategies.
Cloud Security is Someone Else's Problem
Organizations often assume cloud providers handle all security aspects, neglecting their shared responsibility in cloud security models.
Regular Security Assessments
Implement continuous monitoring and regular security assessments to identify vulnerabilities before they can be exploited.
✅ Quick Checks
- What is the primary difference between internal and external threats?
Internal threats have direct access to infrastructure and organizational knowledge, potentially causing greater damage. - Which network type uses consumer-grade routers for basic security?
SOHO (Small Office/Home Office) networks. - What are the three core components of Cisco Secure Data Center solution?
Secure segmentation, threat defense, and visibility. - What does BYOD stand for and why is it significant?
Bring Your Own Device - significant because it blurs traditional network boundaries and requires new security approaches. - Name three common data loss vectors.
Email/social networking, unencrypted devices, and removable media.
📝 Summary
- Network security is critical for business continuity and protecting organizational assets
- Attack vectors can originate from both internal and external sources
- Data loss prevention requires comprehensive controls across multiple vectors
- Different network topologies require tailored security approaches
- Defense-in-depth provides multiple layers of protection
- Cloud and virtualization introduce new security challenges and solutions
- BYOD trends require Mobile Device Management capabilities
- Physical security is crucial for data center protection
References
- Module 1: Securing Networks - Introduction (Ch. 1.0)
- Current State of Affairs (Ch. 1.1)
- Network Topology Overview (Ch. 1.2)
- Cisco Talos Intelligence Group
- Cisco Product Security Incident Response Team (PSIRT)