This module explores Intrusion Prevention Systems (IPS) technologies that provide advanced network security beyond traditional firewalls. Students will learn about different IPS implementations, their deployment methods, and how they integrate with Cisco network infrastructure to detect and prevent sophisticated cyber attacks including zero-day exploits.
📋 Overview
🔑 Key Terms
Zero-Day Attack
Cyberattack exploiting unknown software vulnerabilities that have no available patches or signatures.
HIPS
Host-based Intrusion Prevention System - software installed on individual hosts for local protection.
NIPS
Network-based Intrusion Prevention System - monitors and protects network traffic in real-time.
IDS
Intrusion Detection System - passive monitoring system that alerts on suspicious activity.
SPAN
Switch Port Analyzer - Cisco feature for mirroring traffic to monitoring ports.
Network Tap
Physical device providing passive access to network traffic for monitoring purposes.
IDS and IPS Characteristics
Zero-Day Attacks
Zero-Day Vulnerabilities
Zero-day attacks exploit previously unknown software vulnerabilities, spreading globally within minutes. Traditional firewalls cannot protect against these sophisticated threats, requiring advanced IPS solutions that can detect anomalous behavior patterns.
IDS vs IPS Comparison
| Feature | IDS (Detection) | IPS (Prevention) |
|---|---|---|
| Operation Mode | Passive (out-of-band) | Active (inline) |
| Response | Alert and log only | Block and prevent attacks |
| Network Impact | No performance impact | May add latency |
| Detection Method | Traffic mirroring | Real-time traffic analysis |
⚙️ IPS Implementations
Host-based IPS (HIPS)
Software installed on individual hosts to monitor and analyze suspicious activity:
- OS-specific protection and monitoring
- Application-level security enforcement
- Post-decryption traffic analysis
- Detailed system behavior monitoring
Windows Defender
Combines antivirus, antimalware, and firewall capabilities in a single HIPS solution.
Network-based IPS (NIPS)
Implemented using dedicated devices or routers with IPS capabilities:
- Network-wide visibility and protection
- Real-time traffic analysis
- Centralized signature management
- Scalable deployment options
Promiscuous vs Inline
Promiscuous mode provides passive monitoring, while inline mode enables active threat blocking.
HIPS Advantages and Disadvantages
| Advantages | Disadvantages |
|---|---|
| OS-specific protection | Operating system dependent |
| Application-level monitoring | Must install on all hosts |
| Post-decryption analysis | Limited network visibility |
| Detailed system monitoring | Resource intensive |
IPS on Cisco ISRs
IPS Components
An IPS sensor consists of two main components working together to provide comprehensive threat detection:
- Detection and Enforcement Engine: Validates traffic against known attack signatures
- Attack Signatures Package: Continuously updated database of known threats
Cisco IPS Evolution
Legacy Cisco IOS IPS (800, 1900, 2900, 3900 Series) is no longer supported. Modern deployments use Cisco Snort IPS on 4000 Series ISRs and Cloud Services Routers with updated signature databases.
📊 Network Monitoring Methods
Traffic Capture Methods
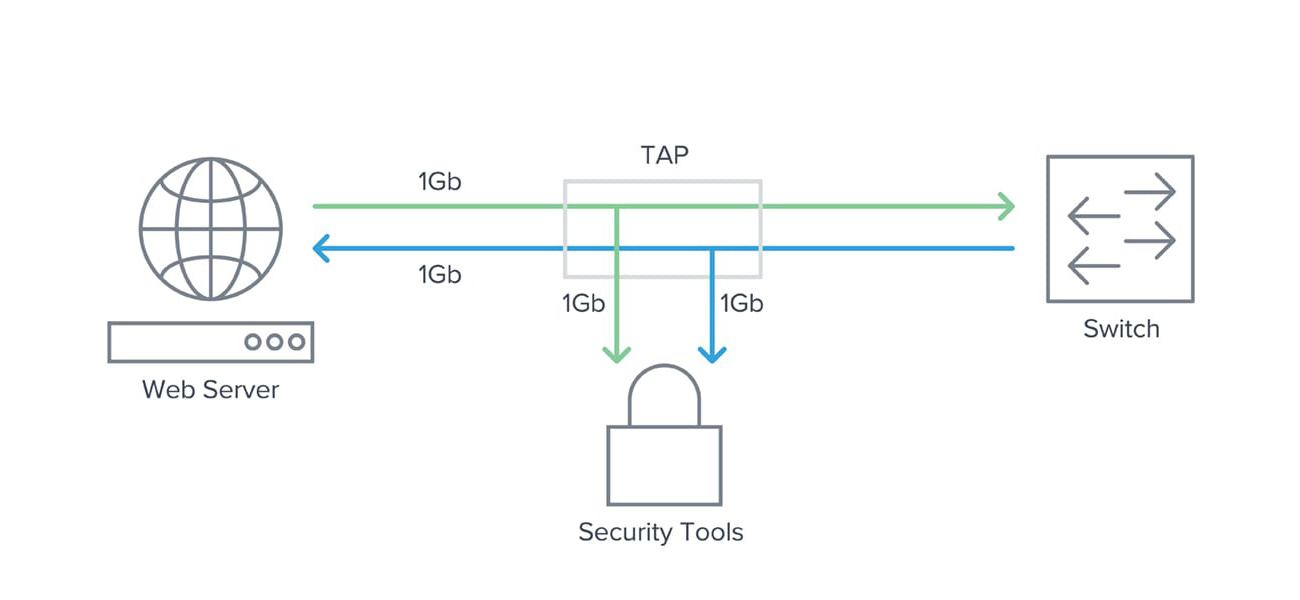
Network Taps
Passive splitting devices implemented inline between network devices:
- Forward all traffic including physical layer errors
- No impact on network performance
- Complete traffic visibility
- Hardware-based reliability
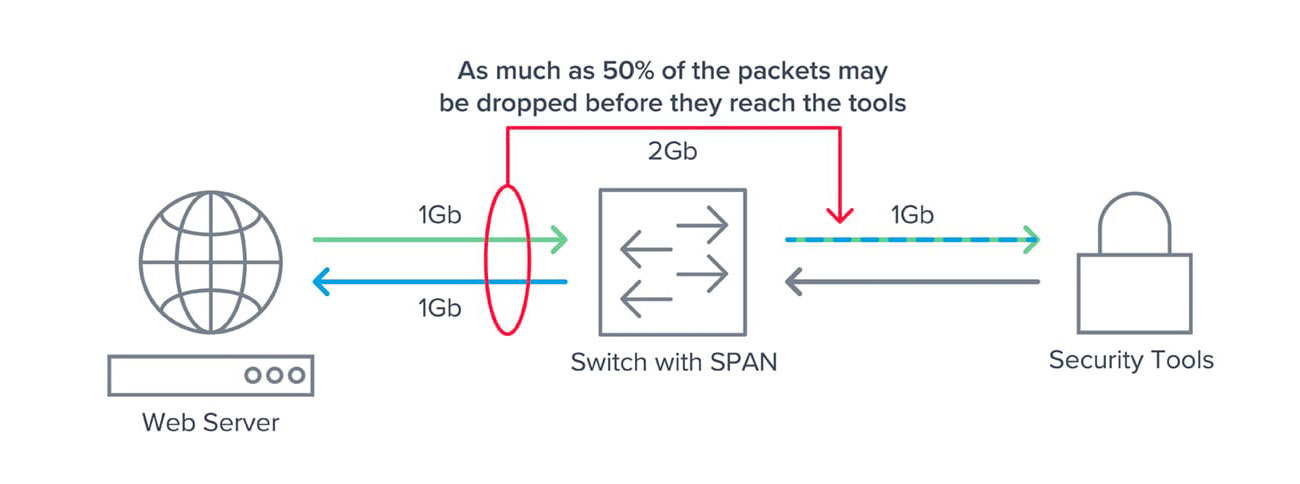
Switch Port Analyzer (SPAN)
Traffic mirroring feature that copies network traffic to monitoring ports:
- More flexible than physical taps
- Software-based configuration
- May not capture all traffic types
- Potential switch performance impact
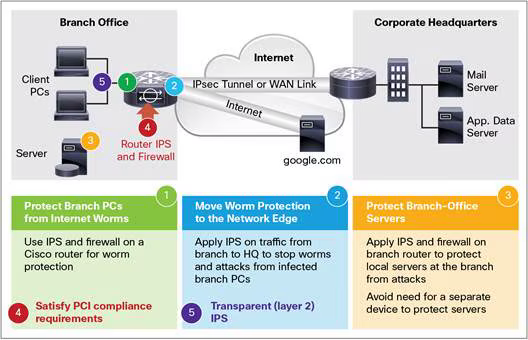
📚 Case Study: Branch Office Protection
Cost-Effective IPS Deployment
A medium-sized company with multiple branch offices implements IPS functionality on existing Cisco ISR routers, achieving 60% cost reduction compared to dedicated IPS appliances while maintaining enterprise-grade security through centralized signature management and real-time threat detection.
This case demonstrates the practical benefits of integrated security solutions, showing how organizations can leverage existing infrastructure to implement comprehensive threat protection without significant additional hardware investment.
⚠️ Common Pitfalls & Misconceptions
Single Point of Failure
Relying solely on perimeter IPS without implementing layered security throughout the network infrastructure.
Set and Forget Mentality
Failing to regularly update attack signature databases and properly tune IPS rules, leading to outdated protection and false positives.
Performance Monitoring
Continuously monitor network latency and throughput when deploying inline IPS to ensure security doesn't compromise network performance.
✅ Quick Checks
- What is the primary difference between IDS and IPS?
IDS operates passively (out-of-band) for detection and alerting, while IPS operates actively (inline) to prevent and block attacks in real-time. - What are the two main types of IPS implementations?
Host-based IPS (HIPS) installed on individual hosts, and Network-based IPS (NIPS) implemented on network devices or dedicated appliances. - Why are zero-day attacks particularly dangerous?
They exploit unknown vulnerabilities that have no available patches, making traditional signature-based detection ineffective until signatures are developed. - What is the advantage of using network taps over SPAN for monitoring?
Taps capture all traffic including physical layer errors and don't impact network performance, while SPAN may miss some traffic and can affect switch performance. - What are the two operating modes for network-based IPS?
Promiscuous mode (passive monitoring like IDS) and Inline mode (active traffic processing and blocking).
📝 Summary
- IPS technologies provide essential protection against sophisticated attacks including zero-day exploits
- Host-based IPS offers detailed system protection but requires installation on all hosts
- Network-based IPS provides network-wide visibility and can operate in promiscuous or inline modes
- Cisco ISRs can be cost-effectively configured as IPS sensors for branch office protection
- Proper network monitoring using taps or SPAN is crucial for effective IPS deployment
- Regular signature updates and proper tuning are essential for optimal IPS performance