This module focuses on the operational aspects of IPS implementation, covering signature-based detection mechanisms and the configuration of Cisco Snort IPS on ISR 4000 series routers. Students will learn how signatures identify malicious traffic, explore different IPS service options, and master the step-by-step configuration process for deploying Snort IPS in enterprise networks.
📋 Overview
🔑 Key Terms
IPS Signature
Set of rules used to detect typical intrusion activity, similar to virus scanner signatures.
Atomic Signature
Simplest signature type that can identify threats within a single packet.
Composite Signature
Complex signature requiring multiple packets and state information to identify threats.
Snort IPS
Open-source intrusion prevention system integrated into Cisco ISR 4000 series routers.
NGIPS
Next-Generation Intrusion Prevention System - dedicated Cisco Firepower appliances.
OVA File
Open Virtualization Archive containing compressed, installable virtual machine.
IPS Signatures
Signature Attributes
IPS signatures have three distinctive attributes that define their behavior:
- Type: Atomic or Composite signature classification
- Trigger: The alarm mechanism that activates the signature
- Action: The response taken when a signature matches
Atomic Signatures
The simplest signature type:
- Identifies threats in a single packet
- Fast processing and low resource usage
- Suitable for known attack patterns
- Limited context awareness
Composite Signatures
Complex signatures requiring multiple packets:
- Analyzes packet sequences and state
- Higher resource requirements
- Better at detecting sophisticated attacks
- Maintains connection state information
Detection Methods
| Method | Description | Use Case |
|---|---|---|
| Pattern-based | Matches specific byte sequences | Known malware signatures |
| Anomaly-based | Detects deviations from normal behavior | Zero-day attacks |
| Policy-based | Enforces security policies | Protocol violations |
| Honey pot-based | Uses decoy systems to attract attacks | Advanced threat detection |
Signature Accuracy
Signature triggering can result in true positives (correct detection), false positives (incorrect alarms), true negatives (correct non-detection), or false negatives (missed threats). Proper tuning is essential.
Cisco Snort IPS
IPS Service Options
Cisco IOS IPS End of Support
Support for Cisco IOS IPS discontinued in 2018. Legacy IOS IPS is no longer recommended on branch routers.
Cisco Firepower NGIPS
Dedicated inline threat prevention appliances:
- Industry-leading effectiveness
- Protection against known and unknown threats
- Built on Snort's core technology
- Vulnerability-focused IPS rules
Cisco Snort IPS
IPS service enabled on ISR 4000 series:
- Integrated routing and security
- Cost-effective branch protection
- Predefined security levels
- Automated signature updates
External Snort IPS Server
Standalone Snort deployment:
- Requires promiscuous port (SPAN)
- External IDS/IPS server
- Flexible deployment options
- Centralized management
Snort IPS Features
Security Levels and Features
Snort IPS offers predefined security levels (connectivity, balanced, security), allow list functionality, engine health monitoring, fail-open/fail-close options, and automated logging with Cisco Talos rule updates.
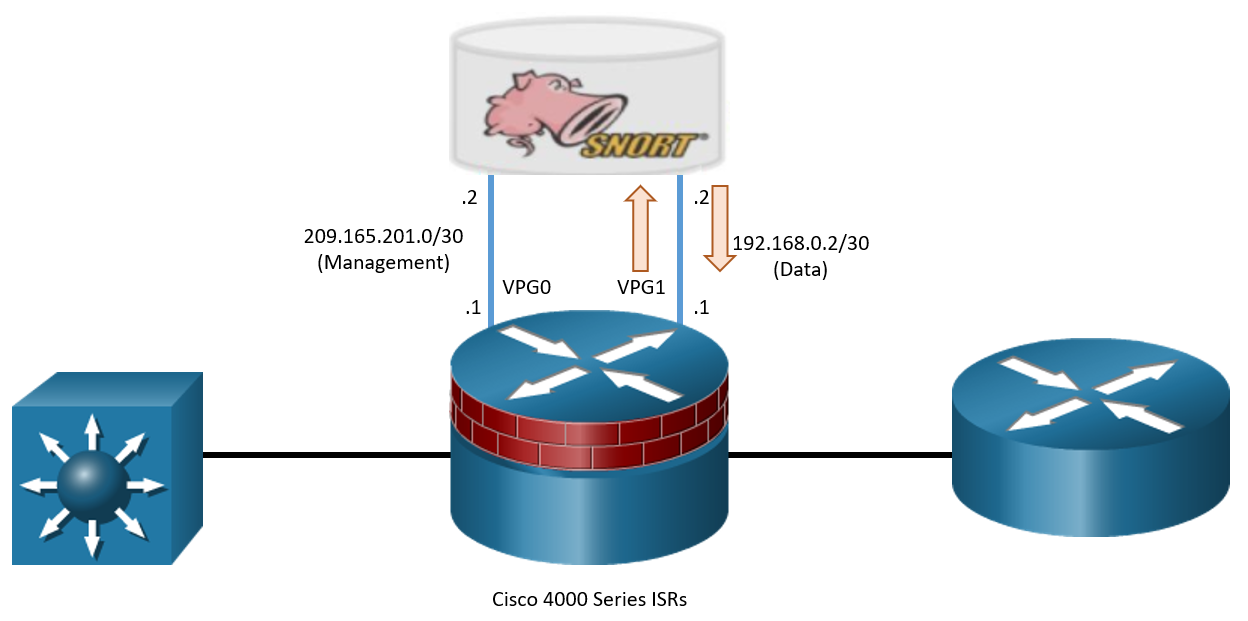

Configure Snort IPS
Configuration Steps
Licensing Requirements
Snort IPS functionality requires security K9-licensed IOS XE version. Available in Cisco IOS XE Release 3.16.1S, 3.17S, and later releases.
- Download the Snort OVA file - Obtain latest OVA from Cisco.com
- Install the OVA file - Deploy virtual machine on router
- Configure Virtual Port Group interfaces - Set up VPG for traffic processing
- Activate the virtual services - Enable Snort service container
- Configure Snort specifics - Set security policies and rules
- Enable IPS globally or on interfaces - Apply UTD (Unified Threat Defense)
- Verify Snort IPS - Use show commands to confirm operation
OVA File Management
OVA Updates
While OVA files may be preinstalled in router flash, it's recommended to download the latest version from Cisco.com to ensure current threat protection capabilities.
Virtual Port Group Configuration
VPG interfaces provide the bridge between physical network traffic and the Snort virtual machine, enabling inline traffic inspection and processing.
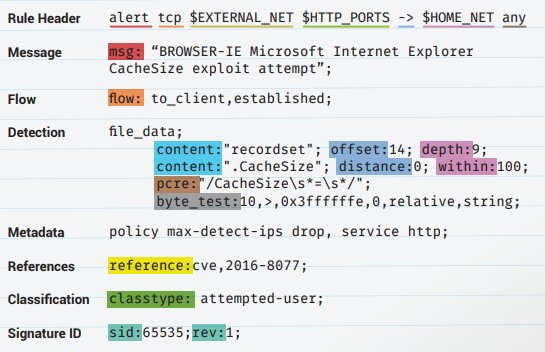
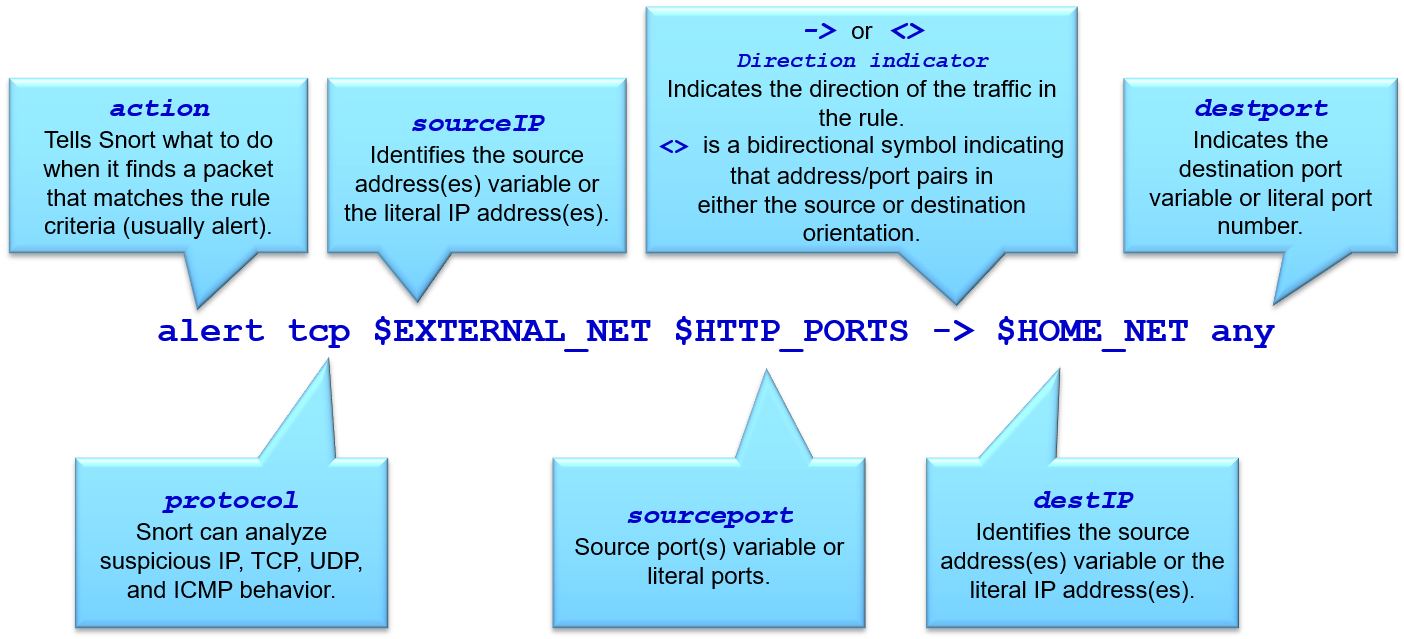
📚 Case Study: Enterprise Branch Security
Multi-Branch Snort IPS Deployment
A financial services company deploys Snort IPS on ISR 4000 routers across 50 branch locations, achieving centralized threat protection with automated Cisco Talos rule updates, reducing security management overhead by 70% while maintaining consistent protection policies.
The implementation demonstrates how organizations can leverage integrated security solutions to provide enterprise-grade protection at branch locations without dedicated security appliances, significantly reducing both capital and operational expenses.
⚠️ Common Pitfalls & Misconceptions
Inadequate Resource Planning
Underestimating CPU and memory requirements for Snort IPS processing, leading to performance degradation during high-traffic periods.
Default Configuration Sufficiency
Assuming default Snort rules provide adequate protection without customization for specific network environments and threat landscapes.
Signature Tuning
Regularly review and tune signature rules to minimize false positives while maintaining effective threat detection capabilities.
✅ Quick Checks
- What are the three attributes of IPS signatures?
Type (atomic or composite), trigger (alarm mechanism), and action (response taken when signature matches). - Why was Cisco IOS IPS discontinued?
Support ended in 2018, replaced by more advanced Snort IPS technology with better threat detection capabilities. - What are the three IPS service options available for modern Cisco networks?
Cisco Firepower NGIPS appliances, Cisco Snort IPS on ISR 4000s, and External Snort IPS servers. - What is required to enable Snort IPS functionality on ISR routers?
Security K9-licensed IOS XE version 3.16.1S, 3.17S, or later releases. - What is the difference between atomic and composite signatures?
Atomic signatures identify threats in single packets, while composite signatures require multiple packets and state information.
📝 Summary
- IPS signatures use type, trigger, and action attributes to identify and respond to threats
- Atomic signatures process single packets while composite signatures analyze packet sequences
- Modern Cisco networks use Firepower NGIPS, Snort IPS on ISR 4000s, or external Snort servers
- Cisco IOS IPS support ended in 2018, replaced by advanced Snort technology
- Snort IPS configuration requires OVA installation, VPG setup, and service activation
- Security K9 licensing is mandatory for Snort IPS functionality
- Proper signature tuning minimizes false positives while maintaining threat detection
- Cisco Talos provides automated rule updates for current threat protection