This module explores the fundamental principles of cryptographic services that form the backbone of modern network security. Students will learn how encryption, hashing, and digital signatures work together to provide confidentiality, integrity, and authentication. The module covers the historical evolution of cryptography, modern cryptanalysis techniques, and the symbiotic relationship between cryptography and cryptanalysis in advancing security technologies.
📋 Overview
🔑 Key Terms
Cryptography
The development and use of codes to protect information from unauthorized access.
Cryptanalysis
The practice of determining encrypted information meaning without access to the shared secret key.
Cryptology
The science of making and breaking secret codes, combining cryptography and cryptanalysis.
Cipher
An algorithm for performing encryption or decryption of data.
Plaintext
Original, unencrypted data that is readable without decryption.
Ciphertext
Encrypted data that appears as random characters without the decryption key.
Secure Communications
Assume Messages Will Be Intercepted
Network communications should always assume that messages will be intercepted. For this reason, encrypted services should be used whenever available, and in many cases, encryption is mandatory.
Three Primary Objectives of Secure Communications
Authentication
Guarantees message authenticity:
- Ensures message is not a forgery
- Confirms authentic source
- Implemented using HMAC
- Prevents impersonation attacks
Integrity
Guarantees message hasn't been altered:
- Similar to checksum function
- Detects unauthorized modifications
- Uses SHA-2 or SHA-3 algorithms
- Ensures data consistency
Confidentiality
Guarantees message privacy:
- Prevents unauthorized deciphering
- Uses symmetric/asymmetric encryption
- Protects sensitive information
- Maintains data secrecy
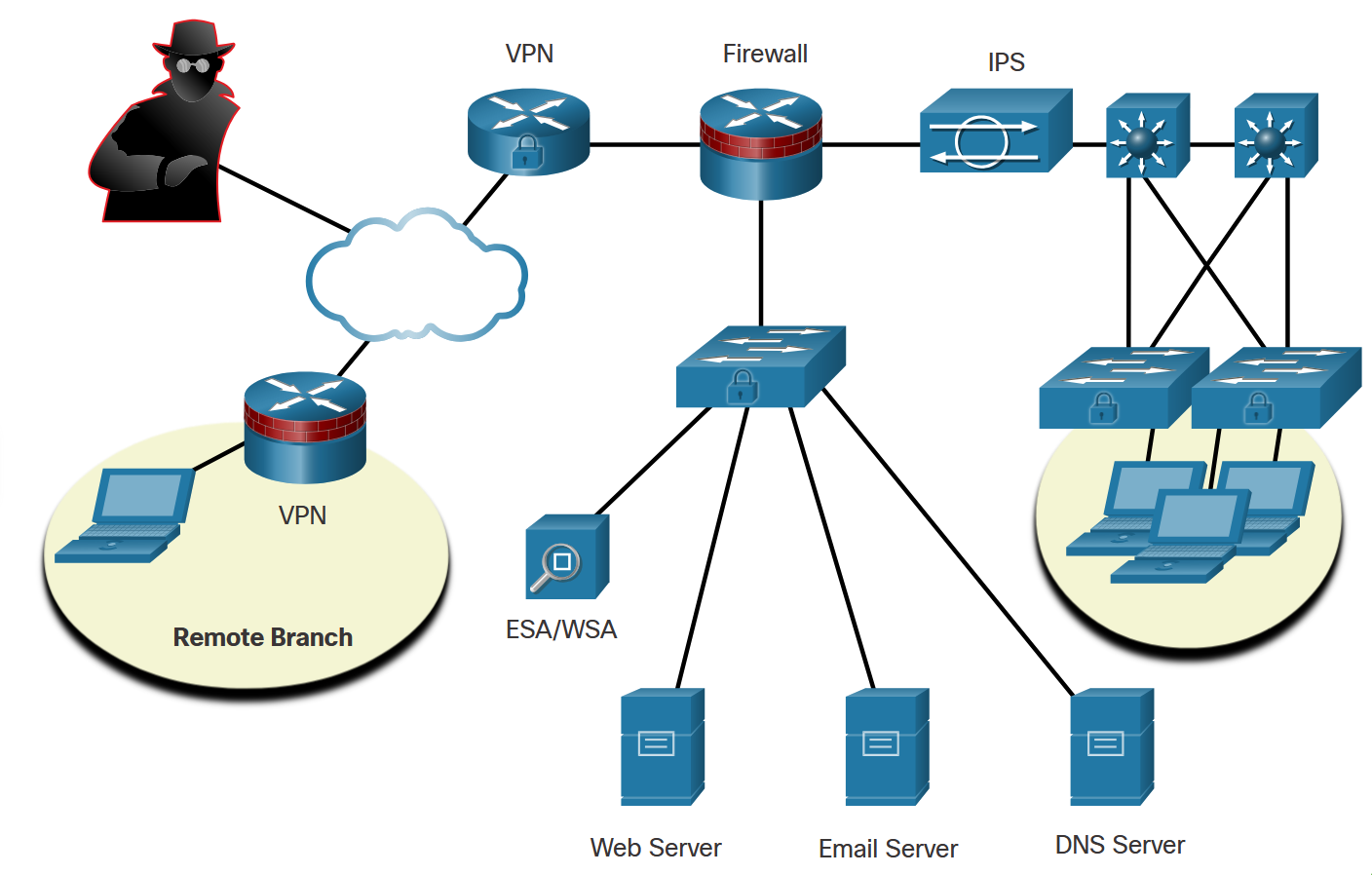
Secure Network Infrastructure
Before securing data transmission, the network infrastructure must be secured using:
- Device hardening and AAA access control
- Access Control Lists (ACLs) and firewalls
- Intrusion Prevention Systems (IPS) for threat monitoring
- Advanced Malware Protection (AMP) for endpoints
- Email Security Appliance (ESA) and Web Security Appliance (WSA)
Cryptography History
Historical Development
Cryptography has been used to secure communications for thousands of years, starting in diplomatic circles where messengers carried encrypted messages between courts.
Historic Cipher Methods
Scytale (Ancient Greece)
Transposition cipher device:
- Paper wrapped around rod of known diameter
- Message written across rows
- Unreadable when unwrapped
- Required same diameter rod to decrypt
Caesar Cipher
Simple substitution cipher:
- Each letter shifted by fixed number
- Easy to implement and understand
- Vulnerable to frequency analysis
- Historical significance in Roman times
Vigenère Cipher
Polyalphabetic substitution cipher:
- Uses keyword for multiple substitutions
- Considered unbreakable until 1863
- Broken by Charles Babbage
- More secure than simple substitution
Enigma Machine
Electro-mechanical encryption device:
- Used by Germans in WWII
- Complex rotor-based system
- Breaking it was turning point in war
- Demonstrated importance of cryptanalysis
Types of Ciphers
| Cipher Type | Method | Example |
|---|---|---|
| Transposition | Rearrange letters without replacement | ATTACK → KCATTA (reverse) |
| Substitution | Replace letters with other letters | Caesar cipher (shift by 3) |
| Polyalphabetic | Multiple substitution alphabets | Vigenère cipher with keyword |
🔍 Cryptanalysis
The Art of Codebreaking
Cryptanalysis in History
Cryptanalysis has changed the course of history: Mary Queen of Scots was executed after her encrypted plot was broken, and breaking the Enigma code was considered a turning point in WWII by Winston Churchill.
Methods of Cryptanalysis
Brute-Force Method
Try every possible key:
- Eventually one key will work
- Success rate ~50% through keyspace
- Time and resource intensive
- All algorithms vulnerable to this
Ciphertext Method
Analyze encrypted messages:
- Has ciphertext of several messages
- No knowledge of underlying plaintext
- Uses statistical analysis
- Frequency analysis techniques
Known-Plaintext Method
Leverage known information:
- Access to both ciphertext and plaintext
- Can deduce encryption patterns
- More effective than ciphertext-only
- Common in wartime scenarios
Chosen-Plaintext Method
Control encryption input:
- Attacker chooses data to encrypt
- Observes resulting ciphertext
- Can test specific patterns
- Powerful analysis technique
Modern Cryptanalysis Objectives
Keyspace Size
Modern cryptographers aim for keyspaces large enough that brute-force attacks require too much time and money to be practical. The goal is computational infeasibility rather than mathematical impossibility.
Cryptanalysis Applications
- Government: Military and diplomatic surveillance
- Enterprise: Testing security procedure strength
- Security Research: Finding vulnerabilities to improve systems
- Malicious Use: Exploiting weaknesses in websites and systems
Modern Cryptology
Cryptology = Cryptography + Cryptanalysis
Mutual Strengthening
Cryptology combines cryptography (making codes) and cryptanalysis (breaking codes). There's a symbiotic relationship where each discipline makes the other stronger. National security organizations employ both and pit them against each other.
Historical Balance
The balance between cryptography and cryptanalysis has shifted throughout history:
- Hundred Years War: Cryptanalysts led cryptographers
- Vigenère Era: France believed their cipher was unbreakable
- WWII: Successful codebreaking had major impact on outcome
- Current Era: Cryptographers are believed to be in the lead
Modern Encryption Technologies
| Technology | Purpose | Examples |
|---|---|---|
| Symmetric Encryption | Fast bulk data encryption | AES, 3DES |
| Asymmetric Encryption | Key exchange, digital signatures | RSA, PKI |
| Hash Functions | Data integrity verification | SHA-2, SHA-3 |
| HMAC | Message authentication | HMAC-SHA256 |
Cryptanalyst Career
Necessary Function
While often linked to malicious purposes, cryptanalysis is actually a necessity. It's an ironic fact that cryptography can only be proven secure by attempting to break it. Cryptanalysts serve essential roles in testing and improving security systems.
📚 Case Study: Enterprise Cryptographic Implementation
Financial Services Encryption
A multinational bank implements end-to-end cryptographic services including AES-256 for data at rest, TLS 1.3 for data in transit, SHA-256 for integrity verification, and RSA-2048 for digital signatures. The implementation ensures compliance with financial regulations while maintaining high-performance transaction processing.
This demonstrates how modern organizations must balance security requirements with operational efficiency, using multiple cryptographic technologies to achieve comprehensive protection across all data states and communication channels.
⚠️ Common Pitfalls & Misconceptions
Relying on Security Through Obscurity
Assuming that keeping encryption methods secret provides security, rather than relying on strong cryptographic algorithms and key management.
Encryption Equals Complete Security
Believing that encryption alone provides complete security without considering key management, implementation flaws, and other attack vectors.
Defense in Depth
Use cryptographic services as part of a comprehensive security strategy that includes multiple layers of protection and proper key management practices.
✅ Quick Checks
- What are the three primary objectives of secure communications?
Authentication (guarantees authentic source), Integrity (ensures message hasn't been altered), and Confidentiality (prevents unauthorized deciphering). - What is the difference between cryptography and cryptanalysis?
Cryptography is the development and use of codes, while cryptanalysis is the practice of breaking those codes without access to the secret key. - Why was the Vigenère cipher considered significant?
It was a polyalphabetic substitution cipher considered unbreakable until Charles Babbage cracked it in 1863, demonstrating that no cipher is permanently secure. - What is the most straightforward cryptanalysis method?
The brute-force method, which tries every possible key until finding the correct one, succeeding on average about 50% through the keyspace. - How do cryptography and cryptanalysis strengthen each other?
They have a symbiotic relationship where cryptanalysis tests and reveals weaknesses in cryptographic systems, leading to stronger encryption methods.
📝 Summary
- Cryptographic services provide authentication, integrity, and confidentiality for secure communications
- Network communications should assume messages will be intercepted and use encryption accordingly
- Cryptography has evolved from simple historical ciphers to complex modern algorithms
- Cryptanalysis has played crucial roles in historical events and continues to strengthen security
- Modern cryptology combines cryptography and cryptanalysis in a symbiotic relationship
- Brute-force attacks target keyspace exhaustion, requiring large key sizes for security
- Multiple cryptanalysis methods exist, from ciphertext-only to chosen-plaintext attacks
- Cryptographic services must be part of comprehensive defense-in-depth strategies