This module focuses on the fundamental cryptographic mechanisms that ensure data integrity and authenticity in digital communications. Students will learn about the four elements of secure communications, explore cryptographic hash functions and their properties, understand key management principles, and examine both symmetric and asymmetric encryption methods for maintaining data confidentiality across network links.
📋 Overview
🔑 Key Terms
Hash Function
One-way mathematical function that produces fixed-length output from variable input data.
HMAC
Hash-based Message Authentication Code using secret key for origin authentication.
Data Integrity
Guarantee that data has not been altered during transmission or storage.
Non-Repudiation
Guarantee that sender cannot deny having sent a message.
Symmetric Encryption
Encryption method using same key for both encryption and decryption.
Asymmetric Encryption
Encryption method using different keys for encryption and decryption.
Secure Communications
Four Elements of Secure Communications
Data Integrity
Guarantees message was not altered:
- Detects changes during transit
- Implemented using SHA-2 or SHA-3
- MD5 should be avoided (insecure)
- Essential for data reliability
Origin Authentication
Guarantees message authenticity:
- Ensures message is not a forgery
- Confirms legitimate source
- Uses HMAC algorithms
- Prevents impersonation attacks
Data Confidentiality
Guarantees message privacy:
- Only authorized users can read
- Uses symmetric/asymmetric encryption
- Prevents eavesdropping
- Essential for sensitive data
Data Non-Repudiation
Guarantees sender accountability:
- Sender cannot deny sending message
- Uses unique sender characteristics
- Provides legal proof of origin
- Critical for business transactions
Universal Encryption
Cryptography can be used almost anywhere that there is data communication. The trend is toward all communication being encrypted to ensure comprehensive security.
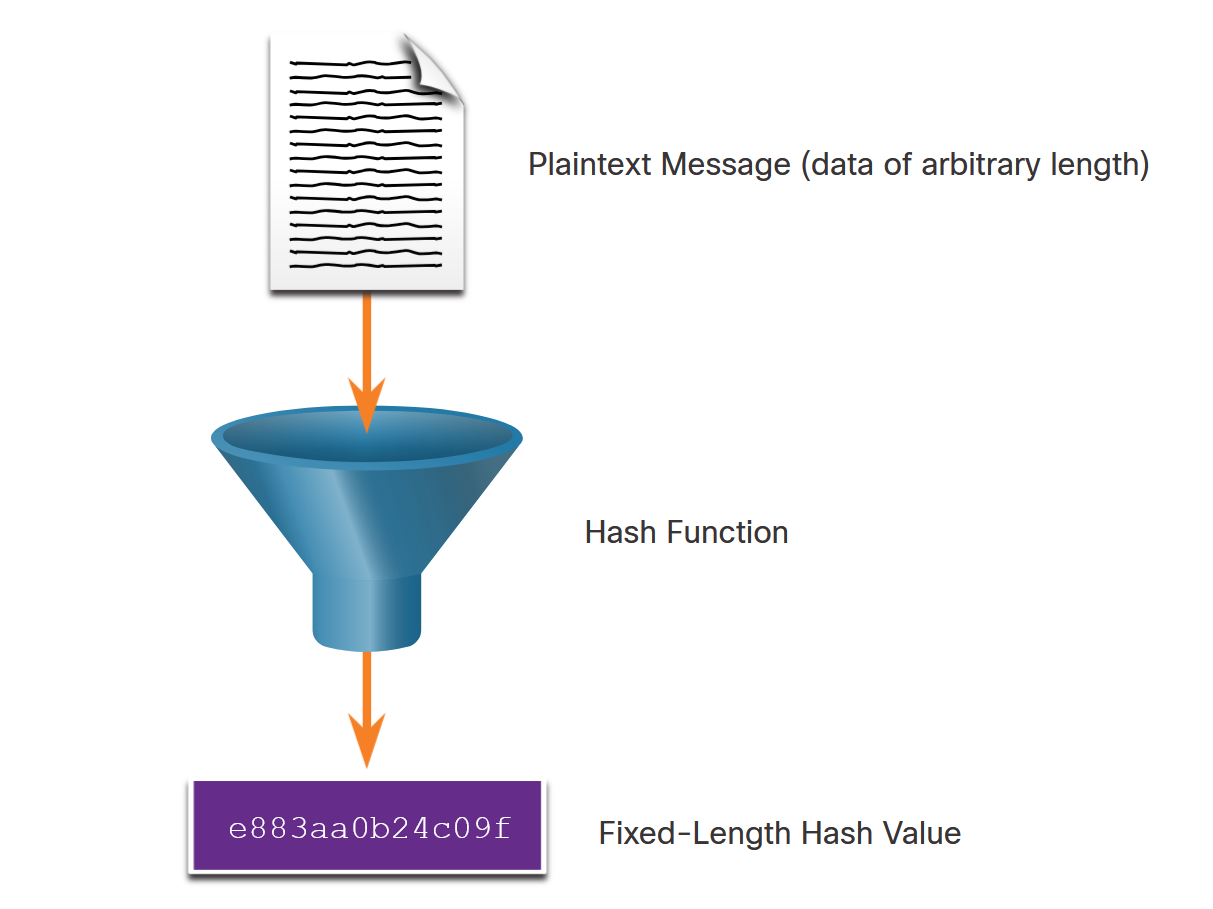
Cryptographic Hash Functions
Hash Function Concept
Coffee Grinding Analogy
Hashing is like grinding coffee beans - easy to grind beans into small pieces, but nearly impossible to reassemble the pieces back into original beans. Hash functions are easy to compute forward but significantly harder to reverse.
Hash Function Properties
A cryptographic hash function should have these essential properties:
- Variable Input: Can accept input of any length
- Fixed Output: Always produces same-length hash
- Easy Computation: H(x) is relatively easy to compute
- One-Way: H(x) is not reversible
- Collision-Free: Different inputs produce different hashes
Mathematical Representation
Hash functions are represented mathematically as: h = H(x)
Where H is the hash function, x is the input message, and h is the resulting fixed-size hash value.
Common Hash Algorithms
| Algorithm | Digest Size | Status | Usage |
|---|---|---|---|
| MD5 | 128 bits | Deprecated | Should be avoided |
| SHA-1 | 160 bits | Deprecated | Legacy systems only |
| SHA-2 | 224-512 bits | Current | Widely used |
| SHA-3 | 224-512 bits | Current | Latest standard |
Hash Function Limitations
Man-in-the-Middle Vulnerability
While hashing can detect accidental changes, it cannot guard against deliberate changes made by threat actors in man-in-the-middle attacks. Origin authentication is required for complete protection.
HMAC for Authentication
Keyed-Hash Message Authentication Code
HMAC uses an additional secret key as input to the hash function, providing both integrity and origin authentication. HMAC is used in SSL, IPsec, and SSH protocols.
📋 Key Management
Most Difficult Aspect
Key management is often considered the most difficult part of designing a cryptosystem. Many cryptosystems have failed due to key management mistakes, and most attacks target key management rather than the algorithms themselves.
Essential Key Management Characteristics
| Characteristic | Description |
|---|---|
| Key Generation | Automated process using good random number generators to ensure all keys are equally likely and unpredictable |
| Key Verification | Procedures to identify and regenerate weak keys that could compromise security |
| Key Storage | Secure storage mechanisms to protect keys from unauthorized access |
| Key Distribution | Secure methods for sharing keys between authorized parties |
| Key Revocation | Procedures for invalidating compromised or expired keys |
| Key Recovery | Backup and recovery mechanisms for critical keys |
Key Management Challenges
- Scalability: Managing keys for large numbers of users
- Distribution: Securely sharing keys across networks
- Lifecycle: Handling key generation, use, and destruction
- Compromise: Detecting and responding to key breaches
Data Confidentiality
Two Classes of Encryption
Symmetric Encryption
Uses same key for encryption and decryption:
- Short key lengths (40-256 bits)
- Faster processing
- Ideal for bulk data encryption
- Used in VPN traffic
- Examples: AES, 3DES
Deprecated Algorithms
DES should not be used. 3DES should be avoided if possible due to security limitations.
Asymmetric Encryption
Uses different keys for encryption and decryption:
- Long key lengths (512-4096 bits)
- Computationally intensive
- Used for key exchange and digital signatures
- Common in HTTPS transactions
- Examples: RSA, PKI
Symmetric vs Asymmetric Comparison
| Aspect | Symmetric | Asymmetric |
|---|---|---|
| Key Usage | Same key for encrypt/decrypt | Different keys for encrypt/decrypt |
| Key Length | 40-256 bits | 512-4096 bits |
| Performance | Fast | Slower |
| Best Use | Bulk data encryption | Key exchange, authentication |
Practical Applications
Best of Both Worlds
Modern systems often use hybrid encryption: asymmetric encryption for secure key exchange, then symmetric encryption for fast bulk data encryption. This combines the security of asymmetric with the performance of symmetric encryption.
📚 Case Study: Banking Security Implementation
Comprehensive Cryptographic Protection
A major bank implements multi-layered cryptographic security: SHA-256 for transaction integrity, HMAC for authentication, AES-256 for data confidentiality, and RSA-2048 for digital signatures. The system processes millions of transactions daily while maintaining regulatory compliance and customer trust.
This implementation demonstrates how the four elements of secure communications work together in practice, providing end-to-end protection for sensitive financial data across multiple communication channels and storage systems.
⚠️ Common Pitfalls & Misconceptions
Using Deprecated Hash Functions
Continuing to use MD5 or SHA-1 despite known vulnerabilities, creating security weaknesses in otherwise secure systems.
Hash Functions Provide Authentication
Believing that hash functions alone provide origin authentication, when they only detect changes and require HMAC for true authentication.
Comprehensive Security Design
Implement all four elements of secure communications (integrity, authentication, confidentiality, non-repudiation) with proper key management for complete protection.
✅ Quick Checks
- What are the four elements of secure communications?
Data integrity, origin authentication, data confidentiality, and data non-repudiation. - Why is MD5 not recommended for cryptographic use?
MD5 is inherently insecure and creates vulnerabilities in networks due to known collision attacks and weaknesses. - What is the main difference between hash functions and HMAC?
Hash functions only provide integrity checking, while HMAC uses an additional secret key to provide both integrity and origin authentication. - Why is key management considered the most difficult part of cryptosystem design?
Many cryptosystems fail due to key management mistakes, and most attacks target key management rather than the cryptographic algorithms themselves. - When would you use symmetric vs asymmetric encryption?
Symmetric encryption for fast bulk data encryption (like VPN traffic), asymmetric encryption for key exchange and digital signatures (like HTTPS handshakes).
📝 Summary
- Four elements of secure communications: integrity, authentication, confidentiality, and non-repudiation
- Hash functions provide one-way mathematical transformation for data integrity verification
- HMAC combines hashing with secret keys for origin authentication
- Key management is the most critical and challenging aspect of cryptosystem design
- Symmetric encryption uses same key for encryption/decryption, ideal for bulk data
- Asymmetric encryption uses different keys, suitable for key exchange and signatures
- Modern systems use hybrid approaches combining symmetric and asymmetric methods
- Deprecated algorithms like MD5 and DES should be avoided in favor of SHA-2/SHA-3 and AES