This module explores Public Key Infrastructure (PKI) and digital signatures as solutions for securing communications with unknown parties and verifying software authenticity. Students will learn how PKI enables secure connections to websites never visited before, how digital signatures provide legal proof of data exchange, and how certificate authorities create scalable trust relationships across the internet.
📋 Overview
🔑 Key Terms
Digital Signature
Mathematical technique providing authenticity, integrity, and non-repudiation using asymmetric cryptography.
PKI
Public Key Infrastructure - framework for creating, managing, and distributing digital certificates.
Certificate Authority (CA)
Trusted third party that issues and manages digital certificates after verifying identities.
Digital Certificate
Electronic passport that authenticates identity and enables secure information exchange.
Code Signing
Process of digitally signing software to verify authenticity and integrity of executable files.
Non-Repudiation
Legal proof that data exchange occurred, preventing sender from denying the transaction.
Digital Signatures
Digital Signature Properties
Authentic
Signature cannot be forged:
- Provides proof of signer identity
- Only legitimate signer can create
- Mathematically verifiable
- Prevents impersonation
Unalterable
Document cannot be changed after signing:
- Any modification invalidates signature
- Ensures data integrity
- Detects tampering attempts
- Maintains original content
Not Reusable
Signature is unique to specific document:
- Cannot be copied to other documents
- Prevents signature replay attacks
- Each signature is document-specific
- Ensures transaction uniqueness
Non-Repudiated
Signer cannot deny creating signature:
- Provides legal proof of transaction
- Prevents denial of participation
- Supports legal proceedings
- Ensures accountability
Common Digital Signature Applications
Code Signing
Verifies software integrity and authenticity:
- Confirms code is from legitimate publisher
- Ensures code hasn't been modified
- Provides publisher accountability
- Prevents malware distribution
Digital Certificates
Virtual ID cards for secure communications:
- Authenticate system identity
- Establish encrypted connections
- Enable secure data exchange
- Support HTTPS and SSL/TLS
Digital Signature Standard (DSS) Algorithms
| Algorithm | Description | Key Features |
|---|---|---|
| DSA | Digital Signature Algorithm | Original standard for key pairs and signatures |
| RSA | Rivest-Shamir-Adleman | Widely used asymmetric algorithm |
| ECDSA | Elliptic Curve DSA | Newer variant with improved efficiency |
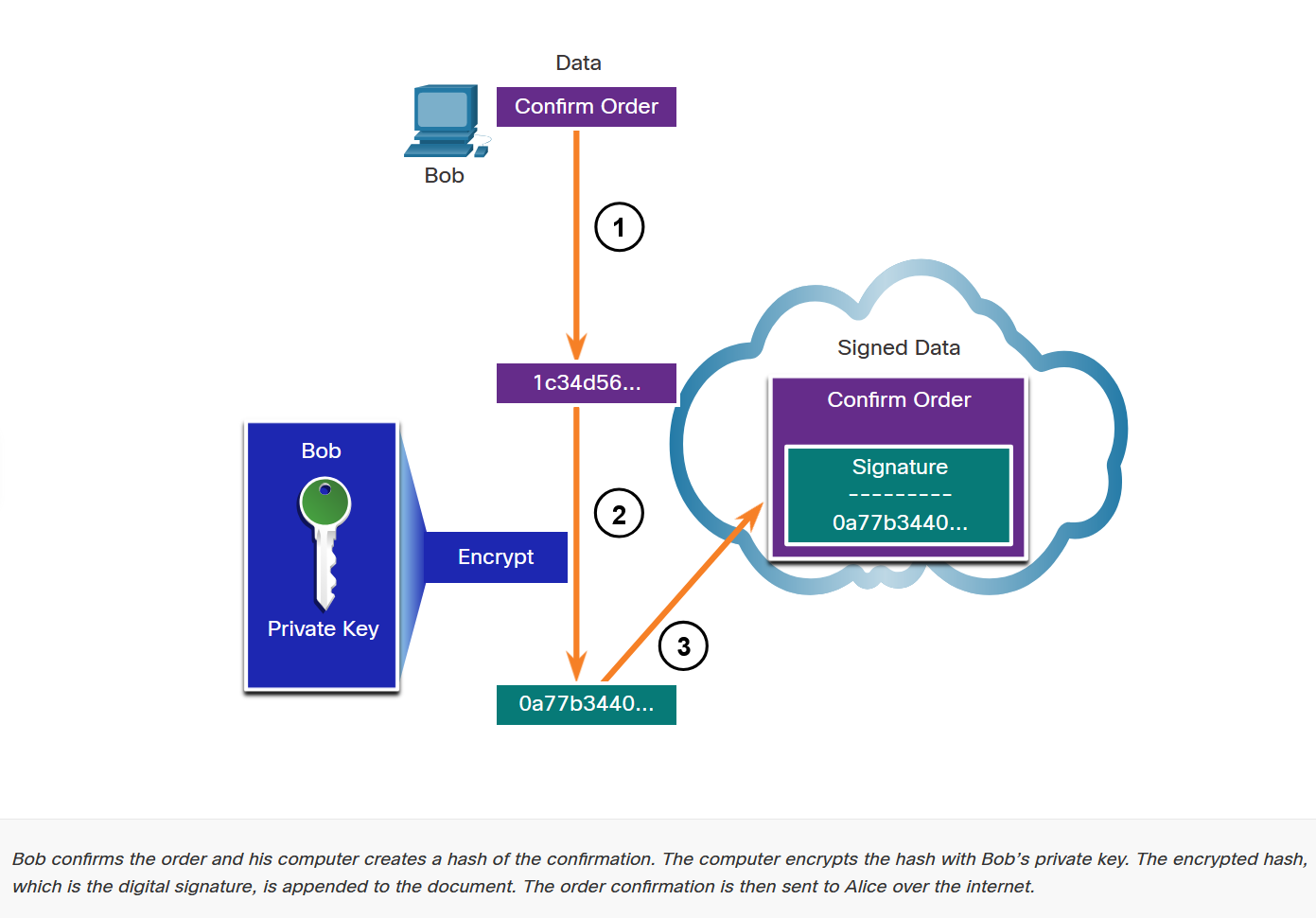
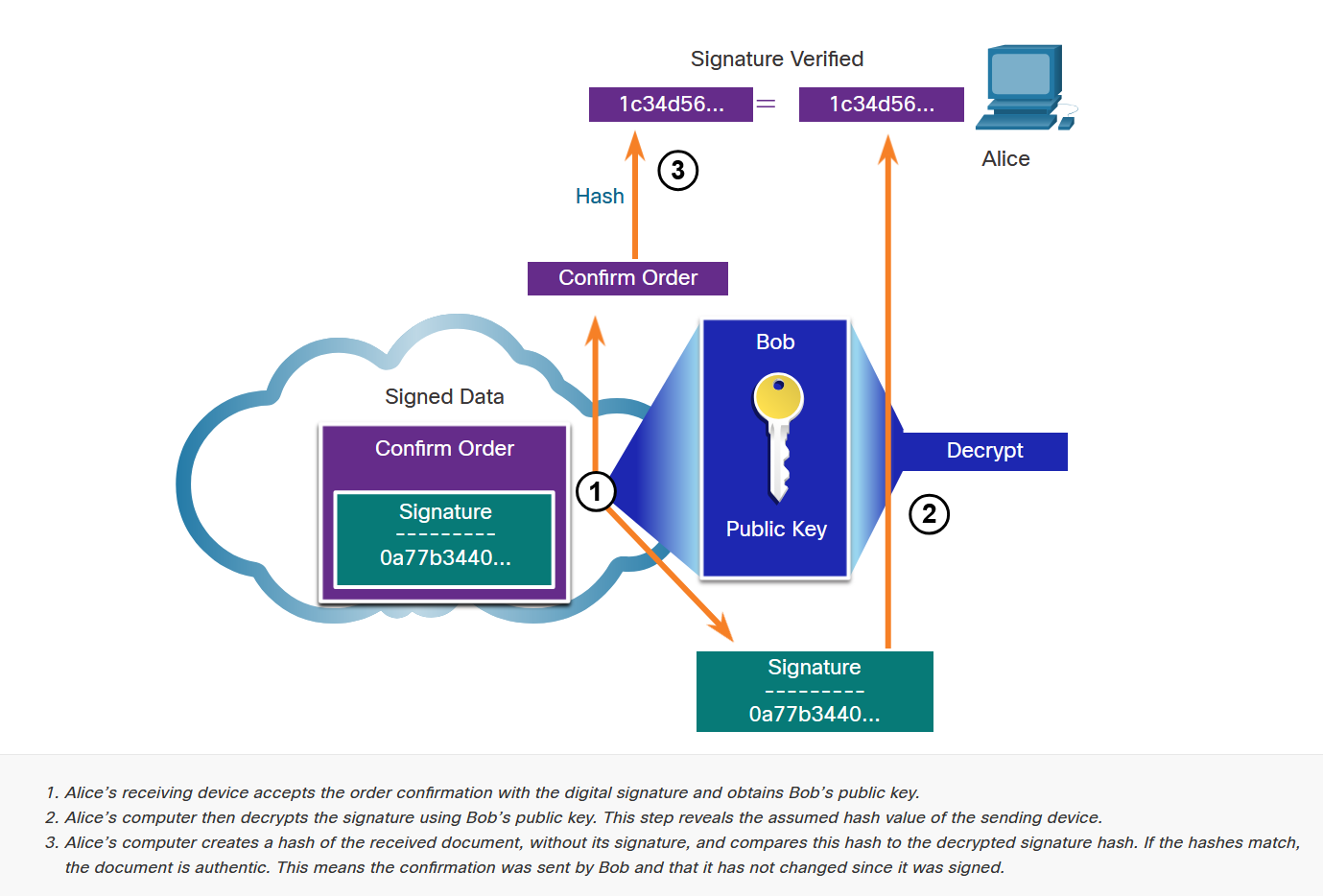
PKI Trust System
Public Key Management Challenge
Verifying Public Key Authenticity
When two hosts establish asymmetric connections, they exchange public keys. The challenge is verifying that these public keys actually belong to the claimed entities and haven't been substituted by attackers.
PKI Framework Components
PKI consists of specifications, systems, and tools used to:
- Create digital certificates and key pairs
- Manage certificate lifecycles and policies
- Distribute certificates and public keys
- Use certificates for authentication and encryption
- Store certificates securely
- Revoke compromised or expired certificates
Driver's License Analogy
Trusted Third Party Model
PKI works like government licensing bureaus: Alice applies for a driver's license, proves her identity through investigation, receives credentials difficult to forge, and others trust these credentials because they trust the issuing authority.
SSL Certificate Process
- Website purchases SSL certificate from trusted CA
- CA performs in-depth identity verification
- CA issues digital certificate with website's public key
- Browser checks certificate validity when connecting
- Browser verifies certificate originated from reliable CA
- Certificate enables secure HTTPS communication
PKI Trust Topologies
Single-Root PKI
The simplest PKI topology uses a single root CA that all entities trust. This creates a hierarchical trust model where trust in the root CA extends to all certificates it issues or validates.
PKI Applications
Enterprise PKI Use Cases
Network Security
PKI enables secure network communications:
- SSL/TLS certificate-based authentication
- IPsec VPN secure tunnels
- HTTPS web traffic encryption
- 802.1x network access control
Application Security
PKI secures applications and data:
- S/MIME secure email protocol
- Secure instant messaging
- Code signing for applications
- Encryption File System (EFS)
Authentication Systems
PKI supports advanced authentication:
- Two-factor authentication with smart cards
- Digital identity verification
- Single sign-on (SSO) systems
- Multi-factor authentication
Data Protection
PKI protects sensitive information:
- USB storage device encryption
- Database encryption
- Document signing and encryption
- Backup and archive protection
Encrypted Traffic Security Challenges
SSL/TLS Traffic Monitoring
The increase in SSL/TLS traffic poses security risks because encrypted traffic cannot be intercepted and monitored by normal means. Users can introduce malware or leak confidential information over encrypted connections, requiring specialized security solutions.
PKI Implementation Considerations
- Scalability: Supporting large numbers of users and devices
- Performance: Managing computational overhead of cryptographic operations
- Compliance: Meeting regulatory and industry standards
- Integration: Working with existing security infrastructure
- Management: Handling certificate lifecycle and revocation
📚 Case Study: E-Commerce PKI Implementation
Online Retail Security
A major e-commerce platform implements comprehensive PKI including EV SSL certificates for customer trust, code signing for mobile apps, S/MIME for secure customer communications, and smart card authentication for administrative access. The system processes millions of secure transactions daily while maintaining PCI DSS compliance.
This implementation demonstrates how PKI enables trust at scale, allowing customers to confidently transact with businesses they've never dealt with before, while providing legal non-repudiation for all parties involved in the transactions.
⚠️ Common Pitfalls & Misconceptions
Ignoring Certificate Validation
Accepting invalid or self-signed certificates without proper validation, undermining the entire PKI trust model.
All CAs Are Equal
Assuming all certificate authorities provide the same level of verification and trustworthiness regardless of their validation procedures.
Certificate Lifecycle Management
Implement proper certificate lifecycle management including regular renewal, revocation procedures, and monitoring for certificate expiration.
✅ Quick Checks
- What are the four properties of digital signatures?
Authentic (cannot be forged), Unalterable (document cannot be changed), Not Reusable (unique to specific document), and Non-repudiated (signer cannot deny). - What are the two main applications of digital signatures?
Code signing (verifying software integrity and authenticity) and digital certificates (virtual ID cards for secure communications). - What is the role of a Certificate Authority in PKI?
CAs are trusted third parties that perform in-depth identity verification and issue digital certificates that are difficult to forge, similar to government licensing bureaus. - What are the three DSS algorithms used for digital signatures?
DSA (Digital Signature Algorithm), RSA (Rivest-Shamir-Adleman), and ECDSA (Elliptic Curve Digital Signature Algorithm). - Why does increased SSL/TLS traffic pose security challenges?
Encrypted traffic cannot be intercepted and monitored by normal security tools, allowing users to potentially introduce malware or leak confidential information over encrypted connections.
📝 Summary
- Digital signatures provide authenticity, integrity, and non-repudiation using asymmetric cryptography
- PKI framework manages creation, distribution, and revocation of digital certificates
- Certificate Authorities act as trusted third parties validating identities before issuing certificates
- Digital signatures are essential for code signing and digital certificate applications
- PKI enables secure communications with previously unknown parties through trust relationships
- Certificate classes indicate verification rigor, with Class 5 being the highest trust level
- PKI applications span network security, application security, authentication, and data protection
- Interoperability challenges exist due to proprietary CA implementations