This module addresses the critical need for secure communications over public networks through Virtual Private Networks (VPNs). Students will learn how VPNs protect against public WiFi vulnerabilities, explore different VPN topologies including site-to-site and remote-access configurations, and understand how IPsec provides comprehensive security through encryption, authentication, and integrity verification for network traffic.
📋 Overview
🔑 Key Terms
VPN
Virtual Private Network - secure tunnel over public networks using encryption for data confidentiality.
IPsec
Internet Protocol Security - IETF standard framework for securing IP communications.
Site-to-Site VPN
VPN connecting entire networks through preconfigured gateway devices.
Remote-Access VPN
VPN enabling individual users to securely connect to enterprise networks.
IKE
Internet Key Exchange - protocol for negotiating IPsec security associations and key management.
Security Association (SA)
Agreement between VPN peers defining security parameters and encryption methods.
📋 VPN Overview
Virtual Private Network Concept
Virtual and Private
A VPN is "virtual" because it carries information within a private network that is actually transported over a public network. It is "private" because the traffic is encrypted to keep data confidential during transport across public infrastructure.
VPN Benefits
Cost Savings
Eliminates need for expensive dedicated circuits:
- Uses existing internet infrastructure
- Reduces telecommunications costs
- Scales without physical infrastructure
- Lower maintenance overhead
Security
Provides enterprise-grade protection:
- Strong encryption algorithms
- Authentication mechanisms
- Data integrity verification
- Protection against eavesdropping
Scalability
Easily accommodates growth:
- Add users without infrastructure changes
- Support for mobile workforce
- Flexible deployment options
- Global connectivity capabilities
Compatibility
Works with existing technologies:
- Integrates with current networks
- Supports multiple protocols
- Cross-platform compatibility
- Standards-based implementation
VPN Components
- Cisco ASA Firewall: Provides secure, high-performance VPN connectivity and always-on access
- SOHO Router: VPN-enabled router providing connectivity back to corporate main site
- Cisco AnyConnect: Client software for remote workers to establish VPN connections
- Business Partner Access: Secure connectivity for external organizations
Early VPN Technologies
Generic Routing Encapsulation (GRE)
Early VPNs were IP tunnels without authentication or encryption. GRE, developed by Cisco, encapsulates IPv4 and IPv6 traffic inside IP tunnels but does not include encryption services, creating virtual point-to-point links without security.
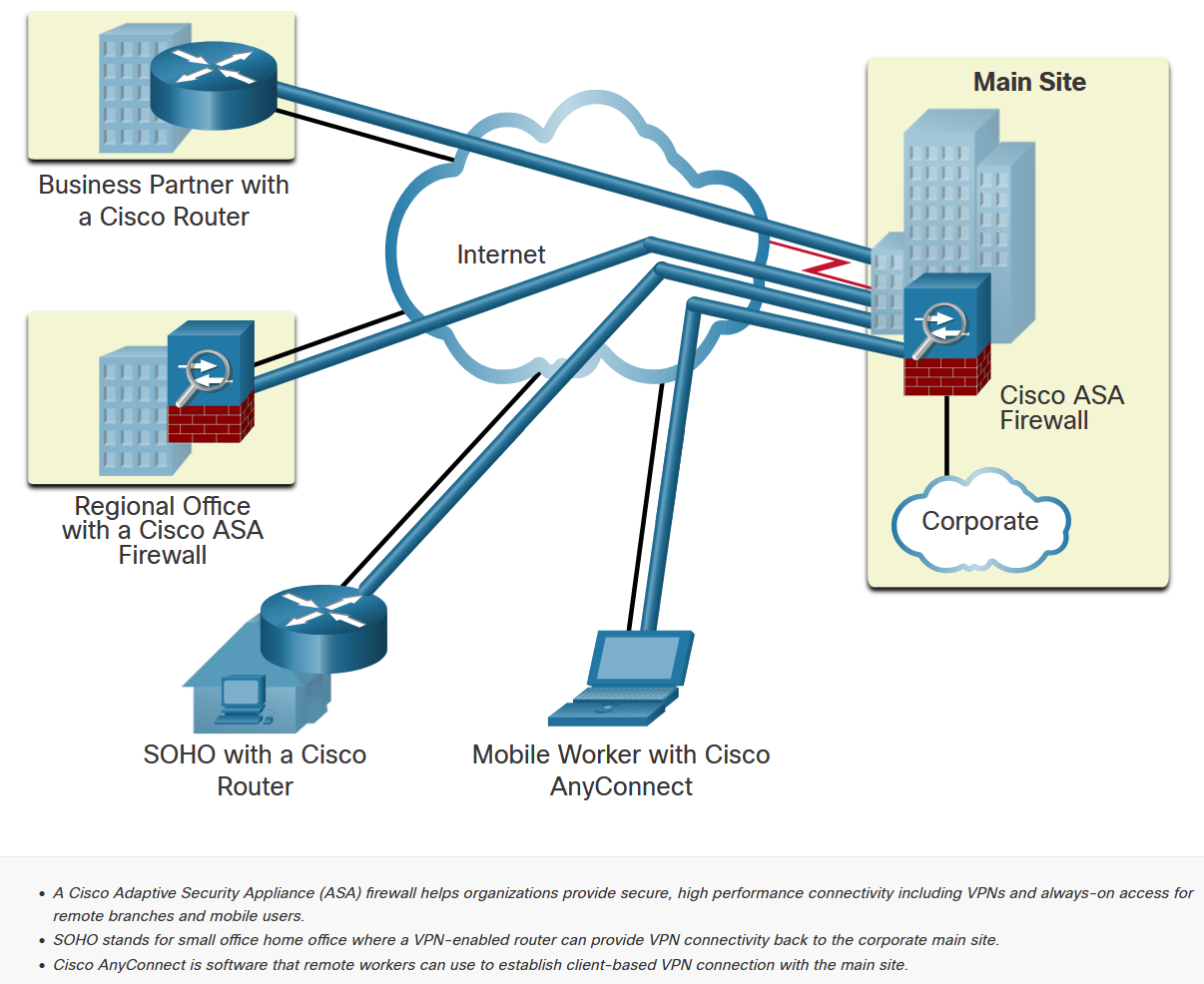
VPN Topologies
Two Main VPN Configurations
Site-to-Site VPN
Connects entire networks securely:
- VPN gateways preconfigured with tunnel information
- Traffic encrypted only between gateway devices
- Internal hosts unaware of VPN existence
- Transparent to end users
- Always-on connectivity
Branch Office Connectivity
Ideal for connecting branch offices to headquarters, providing seamless network access as if all locations were on the same LAN.
Remote-Access VPN
Enables individual user connections:
- Mobile and remote workers
- On-demand connectivity
- User authentication required
- Client software or browser-based
- Flexible access from any location
Remote-Access VPN Types
Clientless VPN
Browser-based secure connections:
- Uses web browser SSL connection
- No client software installation required
- SSL uses PKI and digital certificates
- Authenticates peers automatically
- Limited to web-based applications
Client-Based VPN
Dedicated client application:
- Requires client software installation
- Full network access capabilities
- Examples: Cisco AnyConnect
- Enhanced security features
- Better performance and functionality
VPN Topology Comparison
| Aspect | Site-to-Site | Remote-Access |
|---|---|---|
| Connection Type | Network-to-network | User-to-network |
| Configuration | Preconfigured gateways | User-initiated |
| Transparency | Transparent to users | User-aware connection |
| Scalability | Limited by gateway capacity | Highly scalable |
📋 IPsec Overview
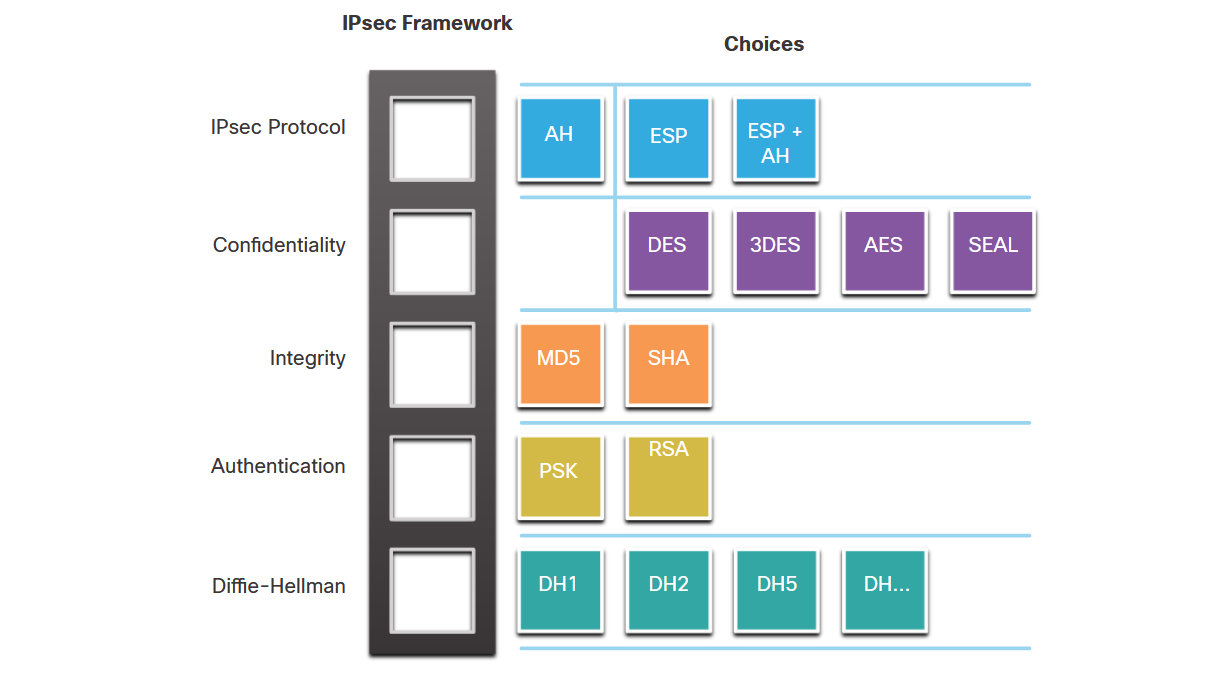
IPsec Framework
RFC 2401-2412
IPsec is an IETF standard that defines how VPNs can be secured across IP networks. It protects and authenticates IP packets between source and destination, covering Layers 4 through 7.
Essential IPsec Security Functions
Confidentiality
Prevents unauthorized data access:
- Uses encryption algorithms
- Prevents cybercriminals from reading packets
- Supports AES, 3DES, SEAL
- Protects sensitive information
Integrity
Ensures data hasn't been altered:
- Uses hashing algorithms
- Detects packet modifications
- Supports SHA, MD5
- Verifies data consistency
Origin Authentication
Verifies source identity:
- Uses Internet Key Exchange (IKE)
- Pre-shared keys (passwords)
- Digital certificates
- RSA certificates
Diffie-Hellman Key Exchange
Secure key establishment:
- Various DH algorithm groups
- Secure key exchange protocol
- Perfect Forward Secrecy
- Prevents key compromise
IPsec Framework Flexibility
Technology Integration
IPsec is not bound to specific protocols, allowing easy integration of new security technologies without updating existing standards. The framework's open slots can be filled with various choices to create unique Security Associations (SAs).
Security Association (SA)
An SA defines the security parameters between VPN peers:
- Encryption algorithms and key lengths
- Authentication methods
- Hash algorithms for integrity
- Key exchange parameters
- Tunnel or transport mode
📡 IPsec Protocols
Two Main IPsec Protocols
Authentication Header (AH)
IP Protocol 51 - Authentication only:
- Provides data authentication and integrity
- Does NOT provide confidentiality
- All text transported unencrypted
- Used when encryption not required/permitted
- Lighter processing overhead
Encapsulation Security Protocol (ESP)
IP Protocol 50 - Full security services:
- Provides both confidentiality and authentication
- Performs encryption on IP packets
- Authenticates inner IP packet and ESP header
- Encryption and authentication are optional
- At minimum, one service must be selected
Protocol Selection Criteria
| Requirement | AH | ESP | ESP + AH |
|---|---|---|---|
| Authentication | ✓ | ✓ | ✓ |
| Integrity | ✓ | ✓ | ✓ |
| Confidentiality | ✗ | ✓ | ✓ |
| Performance | Best | Good | Lowest |
IPsec Framework Components
Modular Architecture
The IPsec framework allows selection of different components for each security function: protocol choice (AH/ESP), confidentiality algorithms (DES/3DES/AES/SEAL), and integrity algorithms (MD5/SHA).
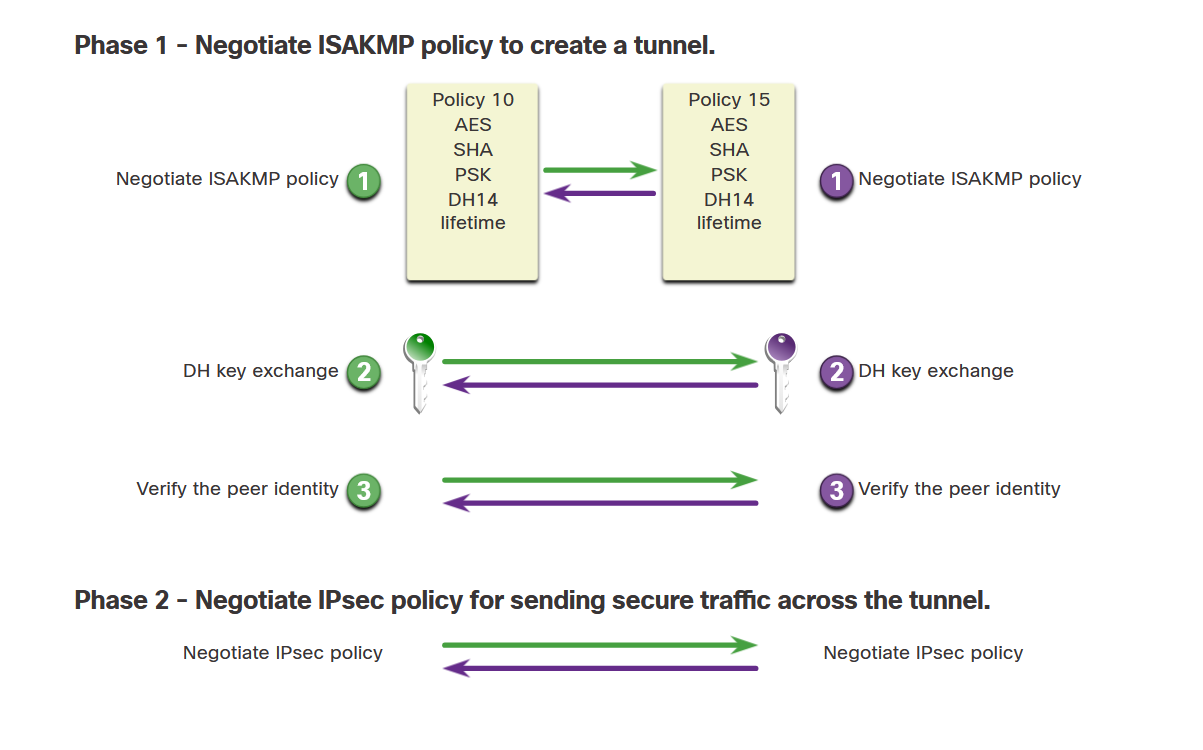
Internet Key Exchange
IKE Protocol Overview
Automated Negotiation
IKE is a key management protocol standard used with IPsec. It automatically negotiates IPsec security associations and enables secure communications. Without IKE, IPsec would require complex manual configuration that doesn't scale well.
IKE Functions
- SA Negotiation: Automatically establishes security associations
- Key Exchange: Securely shares encryption keys between peers
- Authentication: Verifies peer identities
- Parameter Agreement: Negotiates encryption and hash algorithms
- Rekeying: Automatically refreshes keys for ongoing security
IKE Negotiation Process
- Peers initiate IKE negotiation
- Exchange security policies and capabilities
- Authenticate each other using configured method
- Establish shared encryption keys
- Create IPsec security associations
- Begin secure data transmission
Authentication Methods
Pre-Shared Keys (PSK)
Shared password authentication:
- Simple to configure
- Suitable for small deployments
- Requires secure key distribution
- Limited scalability
Digital Certificates
PKI-based authentication:
- Highly scalable
- Strong security
- Requires PKI infrastructure
- More complex to implement
📚 Case Study: Global Enterprise VPN
Multinational Corporation VPN
A global manufacturing company deploys comprehensive VPN infrastructure including site-to-site connections between 50 offices, remote-access VPN for 5,000 mobile workers using Cisco AnyConnect, and partner access for suppliers. The implementation uses IPsec with AES-256 encryption, reducing communication costs by 70% while improving security.
This deployment demonstrates how VPN technologies enable secure global communications, supporting business continuity during the shift to remote work while maintaining enterprise-grade security standards.
⚠️ Common Pitfalls & Misconceptions
Weak Authentication Methods
Using simple pre-shared keys for large deployments instead of implementing proper PKI-based authentication systems.
VPN Equals Complete Security
Assuming VPN connections provide complete security without considering endpoint protection, access controls, and monitoring.
Layered VPN Security
Implement VPNs as part of comprehensive security strategy including endpoint protection, network segmentation, and continuous monitoring.
✅ Quick Checks
- What makes a VPN both "virtual" and "private"?
Virtual because it carries private network information over public networks; private because traffic is encrypted to maintain confidentiality. - What are the two main VPN topology types?
Site-to-site VPNs (connecting entire networks through gateways) and remote-access VPNs (enabling individual users to connect securely). - What are the four essential security functions provided by IPsec?
Confidentiality (encryption), Integrity (hashing), Origin Authentication (IKE), and Diffie-Hellman key exchange. - What is the difference between AH and ESP protocols?
AH provides only authentication and integrity without encryption, while ESP provides both confidentiality and authentication services. - Why is IKE important for IPsec implementations?
IKE automatically negotiates security associations and manages keys, eliminating the need for complex manual configuration that doesn't scale well.
📝 Summary
- VPNs create secure private networks over public infrastructure using encryption
- Site-to-site VPNs connect networks transparently; remote-access VPNs serve individual users
- IPsec framework provides confidentiality, integrity, authentication, and key exchange
- AH protocol provides authentication only; ESP provides both authentication and encryption
- IKE automates security association negotiation and key management
- VPN benefits include cost savings, security, scalability, and compatibility
- Remote-access VPNs can be clientless (browser-based) or client-based (dedicated software)
- Proper authentication methods and endpoint security are critical for VPN deployments