This module provides comprehensive hands-on configuration of the Cisco ASA 5506-X with FirePOWER Services. Students will learn the ASA CLI, configure management settings, implement object groups, create ACLs, configure NAT services, set up AAA authentication, and implement service policies using the Modular Policy Framework. The module also introduces ASDM as a graphical management alternative.
📋 Overview
🔑 Key Terms
ASA CLI
Proprietary command-line interface with similar look and feel to Cisco IOS routers.
Object Groups
Reusable components containing network objects, service objects, or combinations for configuration simplification.
Security Levels
Numerical values (0-100) assigned to interfaces determining default traffic flow permissions.
MPF
Modular Policy Framework - configuration method for applying advanced firewall features to traffic flows.
ASDM
Adaptive Security Device Manager - Java-based GUI tool for ASA configuration and management.
Smart Call Home
Cisco service providing proactive diagnostics and real-time alerts for supported devices.
⚙️ Basic ASA Configuration
ASA CLI Characteristics
IOS-Like Experience
The ASA CLI is a proprietary OS with similar look and feel to Cisco IOS routers, including command prompts, abbreviation support, Tab completion, and help key (?) functionality.
Command Mode Structure
ciscoasa> enable # User EXEC mode
Password:
ciscoasa# configure terminal # Privileged EXEC mode
ciscoasa(config)# # Global configuration mode
ciscoasa(config)# interface g1/1 # Interface configuration mode
ciscoasa(config-if)# exit
ciscoasa(config)#IOS vs ASA Command Differences
| Function | IOS Router Command | ASA Command |
|---|---|---|
| Show interfaces | show ip interface brief |
show interface ip brief |
| Show routing table | show ip route |
show route |
| Configure hostname | hostname name |
hostname name |
| Access lists | Numbered/named ACLs | Named ACLs only |
Default Configuration
SOHO Deployment
The ASA 5506-X ships with a default configuration sufficient for basic SOHO deployment. Configuration can be modified using CLI, Setup Initialization wizard, or ASDM setup wizard.
Factory Reset
ciscoasa(config)# configure factory-default📋 Management Settings
Initial Setup Process
ciscoasa> enable
Password: # Initially blank
ciscoasa# clock set 12:00:00 1 April 2020
ciscoasa# configure terminalSmart Call Home
Cisco Diagnostics Service
Smart Call Home provides proactive diagnostics and real-time alerts on select Cisco devices, offering higher network availability and increased operational efficiency. Requires cisco.com ID and SMARTnet Service contract.
Password Encryption
Default MD5 Encryption
Privileged EXEC password automatically encrypted:
- MD5 hashing by default
- Adequate for basic security
- Legacy encryption method
Enhanced AES Encryption
Stronger encryption configuration:
- Requires primary passphrase
- AES encryption enabled
- Recommended for production
AES Encryption Configuration
ciscoasa(config)# key config-key password-encryption
Enter key: [password]
Re-enter key: [password]
ciscoasa(config)# password encryption aesInterface Configuration
ASA 5506-X has eight Gigabit Ethernet interfaces for different Layer 3 networks:
- G1/1: Frequently configured as outside interface to ISP
- Basic Configuration: IP addressing, naming, security level
- BVI Support: Bridged Virtual Interfaces for grouping
- Security Levels: 0 (outside) to 100 (inside)
Basic Interface Setup
ciscoasa(config)# interface gigabitethernet1/1
ciscoasa(config-if)# nameif outside
ciscoasa(config-if)# security-level 0
ciscoasa(config-if)# ip address dhcp
ciscoasa(config-if)# no shutdownObject Groups
Objects Overview
Configuration Simplification
Objects are reusable components that can be defined once and used throughout configurations. When an object is modified, changes automatically apply to all rules using that object, making configuration maintenance much easier.
Object Types
Network Objects
Define network-related parameters:
- Host addresses
- Network IP addresses and subnets
- IP address ranges
- Fully Qualified Domain Names (FQDN)
object network WEB-SERVER
host 192.168.1.100Service Objects
Define service-related parameters:
- Protocol specifications
- Source port definitions
- Destination port definitions
- Port ranges
object service WEB-SERVICES
service tcp destination eq 80Object Groups
Object groups can contain multiple objects and inline definitions:
- Network Object Groups: Multiple network objects and inline networks/hosts
- Mixed IPv4/IPv6: Support for both address families
- Reusability: Objects can be attached/detached from groups
- Applications: Used in NAT, ACLs, and other policies
Network Object Group Example
object-group network INTERNAL-NETWORKS
network-object 192.168.1.0 255.255.255.0
network-object 192.168.2.0 255.255.255.0
group-object SERVERSBenefits of Objects
- Centralized Management: Modify once, apply everywhere
- Reduced Errors: Consistent definitions across policies
- Simplified ACLs: Readable and maintainable rules
- NAT Requirements: Required for ASA 8.3+ NAT configuration
ASA ACLs
ACL Similarities with IOS
- Made up of Access Control Entries (ACEs)
- Processed sequentially from top down
- Criteria match causes ACL exit
- Implicit deny any at bottom
- Remarks can be added per ACE or ACL
- One ACL per interface, per protocol, per direction
- Time-based ACL support
ASA ACL Differences
Network Masks vs Wildcard Masks
ASA uses network masks (255.255.255.0) instead of wildcard masks (0.0.0.255). ACLs are always named, never numbered. Security levels provide default access control without ACLs.
Types of ACL Filtering
Through-Traffic Filtering
Traffic passing through the ASA:
- From one interface to another
- Two-step configuration process
- Create ACL, then apply to interface
- Controls inter-zone communication
To-the-Box Traffic Filtering
Traffic destined for ASA control plane:
- Management access rules
- SSH, Telnet, HTTPS access
- SNMP and other management protocols
- Applied using management-access command
ACL Configuration Examples
# Standard ACL
access-list OUTSIDE-IN extended permit tcp any host 192.168.1.100 eq 80
access-list OUTSIDE-IN extended deny ip any any
# Apply to interface
access-group OUTSIDE-IN in interface outside
# Management ACL
access-list MGMT-ACCESS extended permit tcp 192.168.1.0 255.255.255.0 any eq ssh
management-access MGMT-ACCESSSecurity Level Behavior
| Traffic Direction | Default Behavior | ACL Required |
|---|---|---|
| Higher to Lower Security | Permitted | No |
| Lower to Higher Security | Denied | Yes |
| Same Security Level | Denied | Yes |
NAT Services
NAT Deployment Methods
Inside NAT
Typical NAT deployment:
- Higher-security to lower-security interface
- Translates internal host to global address
- Restores original IP for return traffic
- Most common implementation
Outside NAT
Reverse NAT deployment:
- Lower-security to higher-security interface
- Makes external host appear internal
- Useful for specific network designs
- Less common implementation
Bidirectional NAT
Combined NAT deployment:
- Both inside and outside NAT together
- Complex translation scenarios
- Advanced network requirements
- Careful planning required
Common NAT Types
| NAT Type | Description | Use Case |
|---|---|---|
| Dynamic PAT | Many-to-one translation with port overload | Internal users to internet |
| Static NAT | One-to-one address translation | Internal servers to outside |
| Policy NAT | Rule-based translation | Conditional translations |
| Identity NAT | Address translated to itself | Bypass NAT for specific traffic |
NAT Configuration Examples
# Dynamic PAT
object network INSIDE-NET
subnet 192.168.1.0 255.255.255.0
nat (inside,outside) dynamic interface
# Static NAT
object network WEB-SERVER
host 192.168.1.100
nat (inside,outside) static 203.0.113.10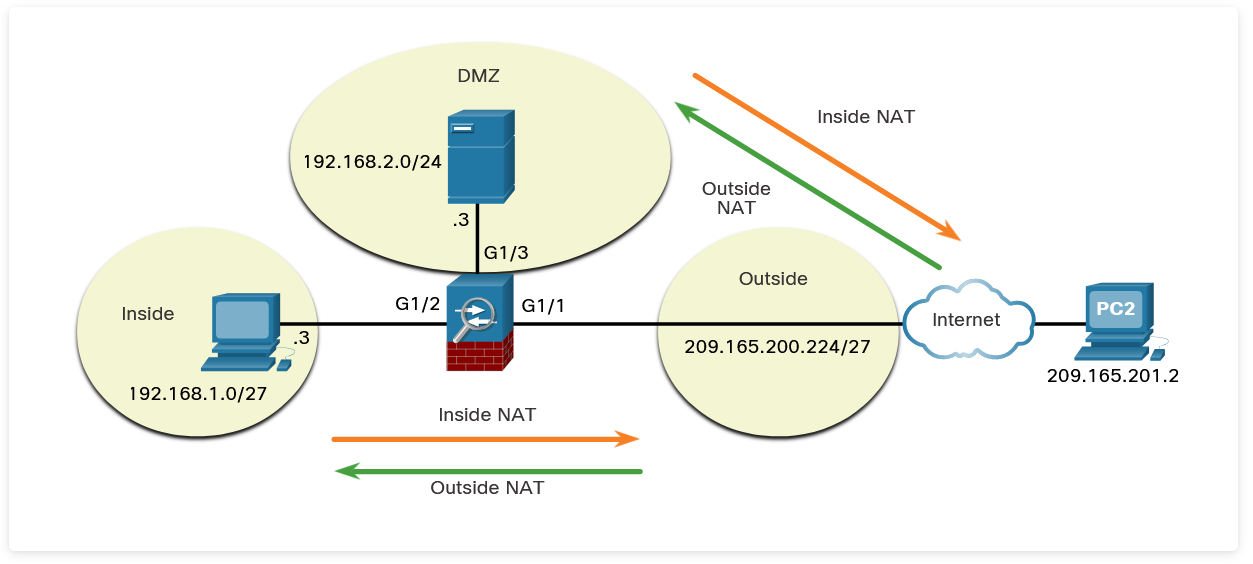
⚙️ AAA Configuration
AAA Overview
Three-Step Process
AAA is like using a credit card: Authentication (Who are you?), Authorization (How much can you spend?), and Accounting (What did you spend it on?). This provides extra protection and user control.
AAA Components
Authentication
Controls access with valid credentials:
- Username and password verification
- Administrative connections (SSH, Telnet, HTTPS)
- Console and privileged EXEC access
- Can be used alone or with authorization
Authorization
Controls per-user access after authentication:
- Service and command availability
- Management command authorization
- Network and VPN access control
- Always requires authentication first
Accounting
Tracks user activity and traffic:
- Session start and stop times
- Username and byte count tracking
- Service usage and session duration
- Can be used alone or with auth/authz
Authentication Methods
Local Database
ASA-based user storage:
- Users stored on ASA
- Simple to configure
- Limited scalability
- No external dependencies
username admin password P@ssw0rd
username admin attributes
privilege-level 15External Servers
Centralized authentication:
- RADIUS or TACACS+ servers
- Highly scalable
- Centralized management
- Advanced authorization features
aaa-server RADIUS-GROUP protocol radius
aaa-server RADIUS-GROUP (inside) host 192.168.1.50
key SharedSecret123AAA Configuration Example
# Enable AAA for SSH
aaa authentication ssh console LOCAL
ssh 192.168.1.0 255.255.255.0 inside
ssh timeout 10
# Enable AAA for HTTP management
aaa authentication http console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 insideService Policies
Modular Policy Framework (MPF)
Granular Policy Application
MPF defines rules for applying firewall features like traffic inspection and QoS to traffic traversing the ASA. It enables granular classification of traffic flows and application of different advanced policies to different flows.
MPF Configuration Objects
Class Maps
What are we looking for?
- Classify and identify traffic
- Layer 3 and 4 classification
- Multiple match criteria support
- Traffic identification for MPF
class-map VOICE-TRAFFIC
match port tcp eq 5060Policy Maps
What do we do with it?
- Define actions for classified traffic
- Inspection, QoS, rate limiting
- Layer 5-7 application inspection
- Advanced security services
policy-map VOICE-POLICY
class VOICE-TRAFFIC
inspect sipService Policy
Where do we apply it?
- Apply policy maps to interfaces
- Global or interface-specific
- Activate configured policies
- Enable traffic processing
service-policy VOICE-POLICY interface insideMPF Capabilities
- Application Inspection: Layer 5-7 protocol analysis
- QoS Features: Traffic prioritization and rate limiting
- Hardware Module Integration: Redirect traffic to specialized modules
- Advanced Policies: Richer feature set than ISR Zone-Based Firewall
Complete MPF Example
# Class map to identify HTTP traffic
class-map WEB-TRAFFIC
match port tcp eq 80
# Policy map to inspect HTTP
policy-map INSPECTION-POLICY
class WEB-TRAFFIC
inspect http
class inspection_default
inspect icmp
# Apply globally
service-policy INSPECTION-POLICY global📋 ASDM Overview
ASDM Benefits
Simplified Configuration
ASDM is a Java-based GUI tool that simplifies ASA setup, configuration, monitoring, and troubleshooting. It hides command complexity and provides streamlined configurations without requiring extensive CLI knowledge.
ASDM Features
- Intuitive Interface: Graphical configuration wizards
- SSL Security: Secure communication with ASA
- Quick Configuration: Wizards for common tasks
- Monitoring: Real-time logging and monitoring
- Troubleshooting: Built-in diagnostic tools
ASDM vs CLI
| Aspect | CLI | ASDM |
|---|---|---|
| Learning Curve | Steep, requires command knowledge | Intuitive, GUI-based |
| Speed | Fast for experienced users | Slower but more guided |
| Features | All features available | Most features with wizards |
| Automation | Scriptable | Limited automation |
ASDM Prerequisites
Runtime Environment
ASDM requires Java Runtime Environment (JRE) installation on the management host. Due to Oracle Java license changes, JRE installation may have restrictions in lab environments.
ASDM Access Configuration
# Enable HTTP server for ASDM
http server enable
http 192.168.1.0 255.255.255.0 inside
# Create management user
username admin password P@ssw0rd
username admin attributes
privilege-level 15FirePOWER Management
Firepower Management Center (FMC)
For advanced features of the ASA FirePOWER module included with ASA 5506-X, Firepower Management Center (FMC) is recommended over ASDM for comprehensive threat management.
📚 Case Study: Small Business ASA Deployment
Professional Services Firm
A 25-employee professional services firm implements comprehensive ASA 5506-X configuration including object groups for network management, ACLs for security policies, NAT for internet access, AAA with RADIUS authentication, and MPF for application inspection. The deployment provides enterprise-grade security with simplified management.
This implementation demonstrates how proper ASA configuration provides layered security while maintaining usability, showing the importance of systematic configuration approach and the benefits of using objects and policies for maintainable security infrastructure.
⚠️ Common Pitfalls & Misconceptions
Ignoring Object Groups
Creating inline definitions instead of using reusable objects, making configuration maintenance difficult and error-prone.
Security Levels Provide Complete Protection
Assuming default security level behavior eliminates the need for proper ACL design and implementation.
Systematic Configuration Approach
Use objects and object groups consistently, implement proper ACLs regardless of security levels, and document all configuration changes for maintainability.
✅ Quick Checks
- What are the main differences between ASA and IOS ACLs?
ASA uses network masks instead of wildcard masks, ACLs are always named (never numbered), and security levels provide default access control without ACLs. - What are the benefits of using object groups in ASA configuration?
Centralized management (modify once, apply everywhere), reduced errors through consistent definitions, simplified ACLs, and required for NAT in ASA 8.3+. - What are the three components of the Modular Policy Framework?
Class maps (classify traffic), Policy maps (define actions), and Service policies (apply to interfaces). - What is the difference between through-traffic and to-the-box traffic filtering?
Through-traffic filtering controls traffic passing between interfaces, while to-the-box filtering controls traffic destined for the ASA control plane (management access). - What are the four common types of NAT supported by ASA?
Dynamic PAT (many-to-one with overload), Static NAT (one-to-one), Policy NAT (rule-based), and Identity NAT (address translated to itself).
📝 Summary
- ASA CLI provides IOS-like interface with proprietary commands and network mask usage
- Object groups enable reusable, maintainable configurations for networks and services
- ASA ACLs use network masks, are always named, and work with security level defaults
- NAT services support dynamic PAT, static NAT, policy NAT, and identity NAT
- AAA provides authentication, authorization, and accounting using local or external databases
- MPF enables granular traffic classification and advanced policy application
- ASDM offers GUI-based management alternative to CLI configuration
- Systematic configuration approach using objects and policies improves maintainability